Authenticating DigitalOcean for Terraform OSS
Scenario
Why?
I’m diving into Terraform as part of my adventure into the DevOps world, which I’ve adopted an interest in the past few months.
- I use 2 workstations with DigitalOcean
- MacBook; for when I’m out and about
- ArchLinux; for when I’m at home
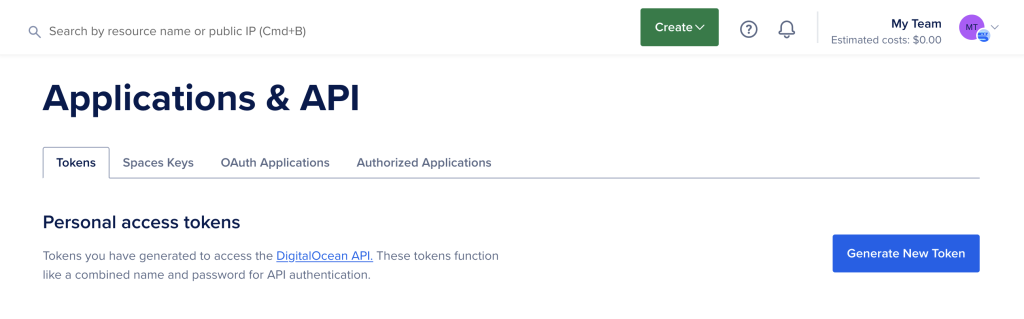
Generating the API Tokens
Under API, located within the dashboards’ menu (on the left-hand side), I’m presented with the option to Generate New Token.
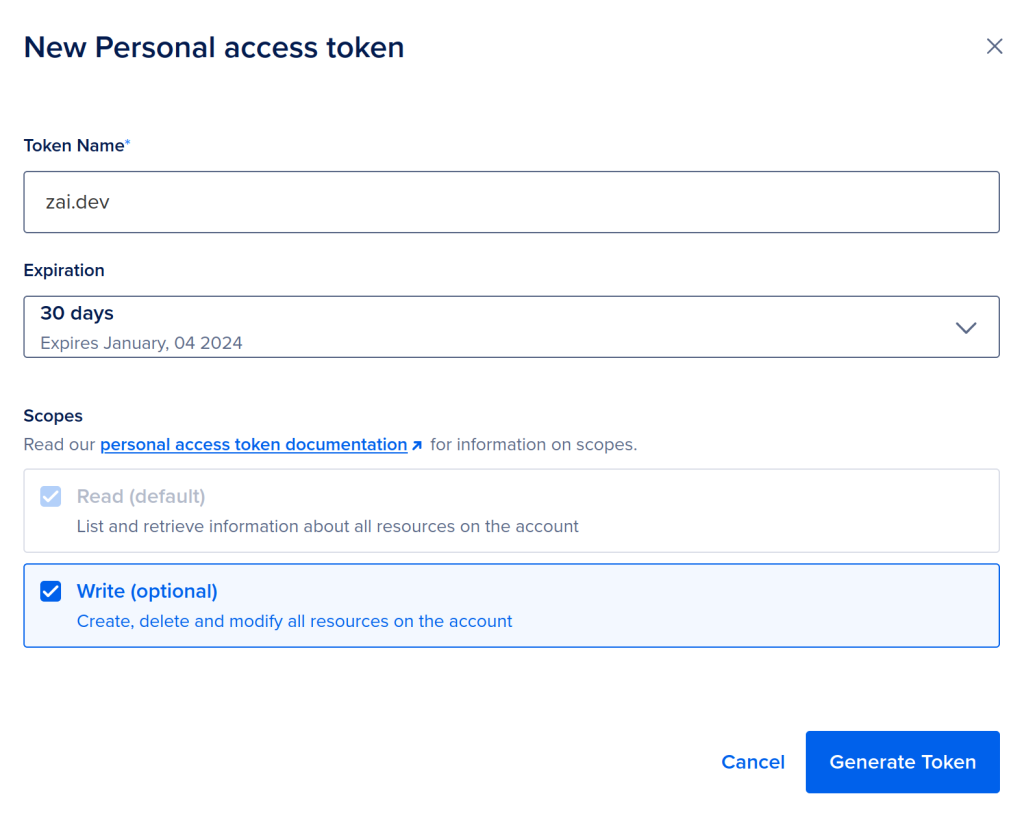
Followed by an interface to define;
- Name
- I typically name this token as
zai.devorpersonal, as this token will be shared across my devices. While this approach isn’t the most secure (Ideally, I should have one token per machine), I’m going for the matter of convenience of having one token for my user profile.
- I typically name this token as
- Expiry date
- Since I’m sharing the token across workstations (including my laptop, which may be prone to theft), I set the expiration to the lowest possible value of 30 days.
- Write permissions
- Since I’ll be using Terraform, and it’s main purpose is to ‘sculpt’ infrastructure, I require the token that it’ll use to connect to DigitalOcean to have write permissions.
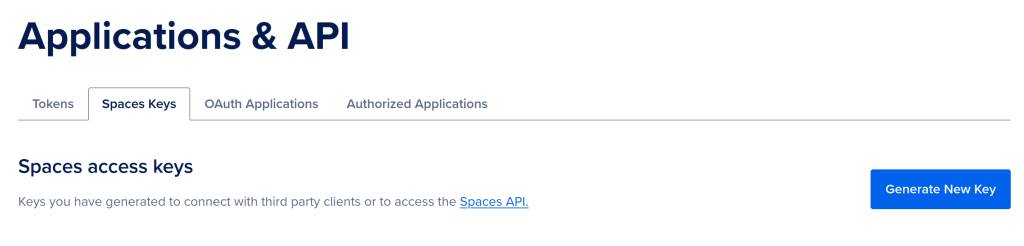
Authenticating DigitalOcean Spaces
As the Terraform Provider allows the creation of Spaces, DigitalOceans’ equivalent to AWS’ S3-bucket, I should also create tokens for it. By navigating to the “Spaces Keys” tab under the APIs option, I can repeat the same steps as above
Installing the Tokens
Continuing from the setup of environment variables in my Synchronizing environment variables across Workstations post, I need to add 3 environment variables for connecting to DigitalOcean.
DIGITALOCEAN_TOKEN- This is the value that is given to you after hitting “Generate Token” on the Tokens tab
SPACES_ACCESS_KEY_ID- This is the value that is given to you after hitting “Generate Token” on the Spaces Tokens tab
SPACES_SECRET_ACCESS_KEY- This is the one-time value that is given to you alongside the
SPACES_ACCESS_KEY_IDvalue
- This is the one-time value that is given to you alongside the
Whilst I’m at it, I’m going to add the following environment variables so that I can use any S3-compliant tools to communicate with my object storage, such as the s3 copy command to push build artifacts
AWS_ACCESS_KEY_ID=${SPACES_ACCESS_KEY_ID}AWS_SECRET_ACCESS_KEY=${SPACES_SECRET_ACCESS_KEY}
To keep things tidy, I created a separate environment file for digital ocean, under ~/.config/zai/env/digitalocean.sh
export DIGITALOCEAN_TOKEN="<DO_TOKEN>"
export SPACES_ACCESS_KEY_ID="<SPACES_KEY>"
export SPACES_SECRET_ACCESS_KEY="<SPACES_SECRET>"
export AWS_ACCESS_KEY_ID=${SPACES_ACCESS_KEY_ID}
export AWS_SECRET_ACCESS_KEY=${SPACES_SECRET_ACCESS_KEY}
